Analyzing DNS Traffic
Point3 CTF Writeup
Name of challenge: greatorange
This requirements for this challenge were to analyze a PCAP file to find the flag. The PCAP file is a list of DNS traffic (UDP packets).
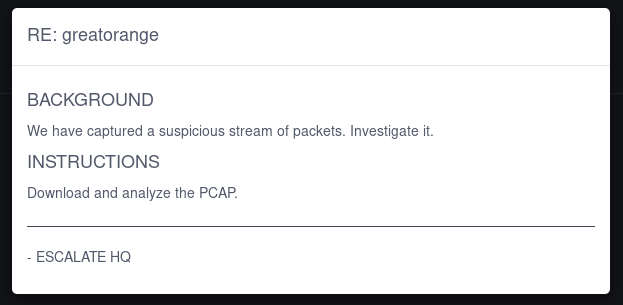
Note: DNS functions in a query-response format. In a nutshell, when a client wishes to resolve a DNS name to an IP address, it sends a query to a DNS server. The server sends the requested info in its response.
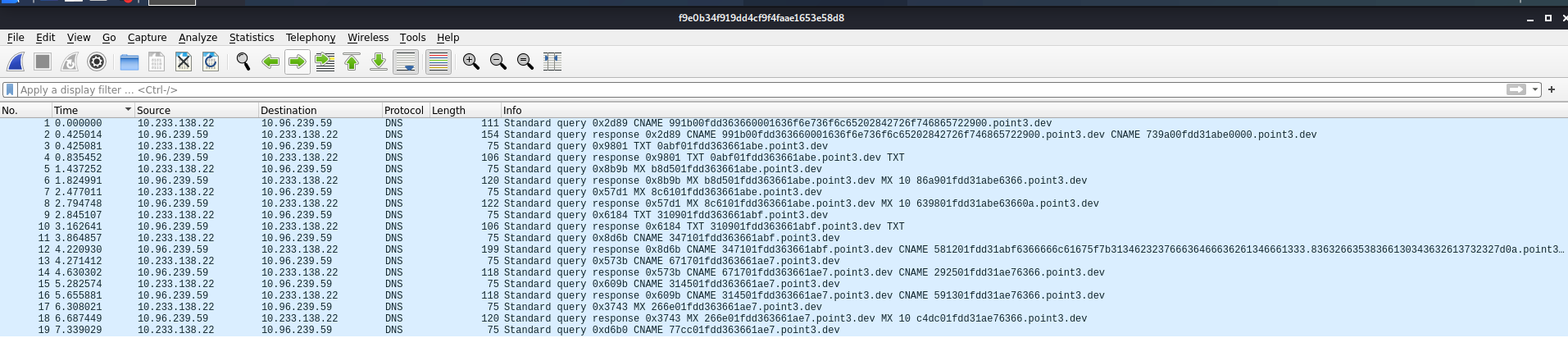
The DNS resource types being queried in this PCAP traffic are CNAME, MX, and TXT records. The traffic is particularly unusal because the subdomains are encoded using hex. We need to extract the hex values and see what it decodes to.
We can use tshark to extract all of the subdomains, which are contained in the request, response and cname names. The following command will retrieve those names and write to a file.
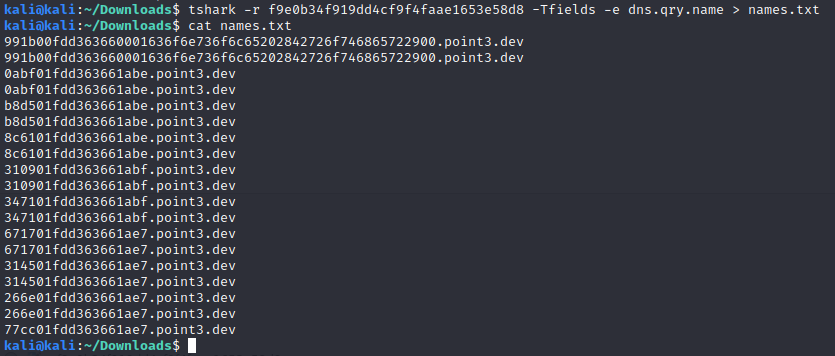
Then using the xxd command we can decode the hex string and convert to ASCII. The flag is now deciphered.
flag_{14b27fcdfcba4fa3862f586a0462a722}