Network Forensics and Word Docs
Point3 CTF Writeup
Name of challenge: warmsong
I really enjoyed the Network forensics category in the Point3 CTF. Finding the solution to this challenge required analyzing and extracting a Word document from a pcap file.
I opened the pcap file provided for me in Wireshark and there was an entry that stuck out like a sore thumb. The item in question was an HTTP transfer that had the content type of an Office document.
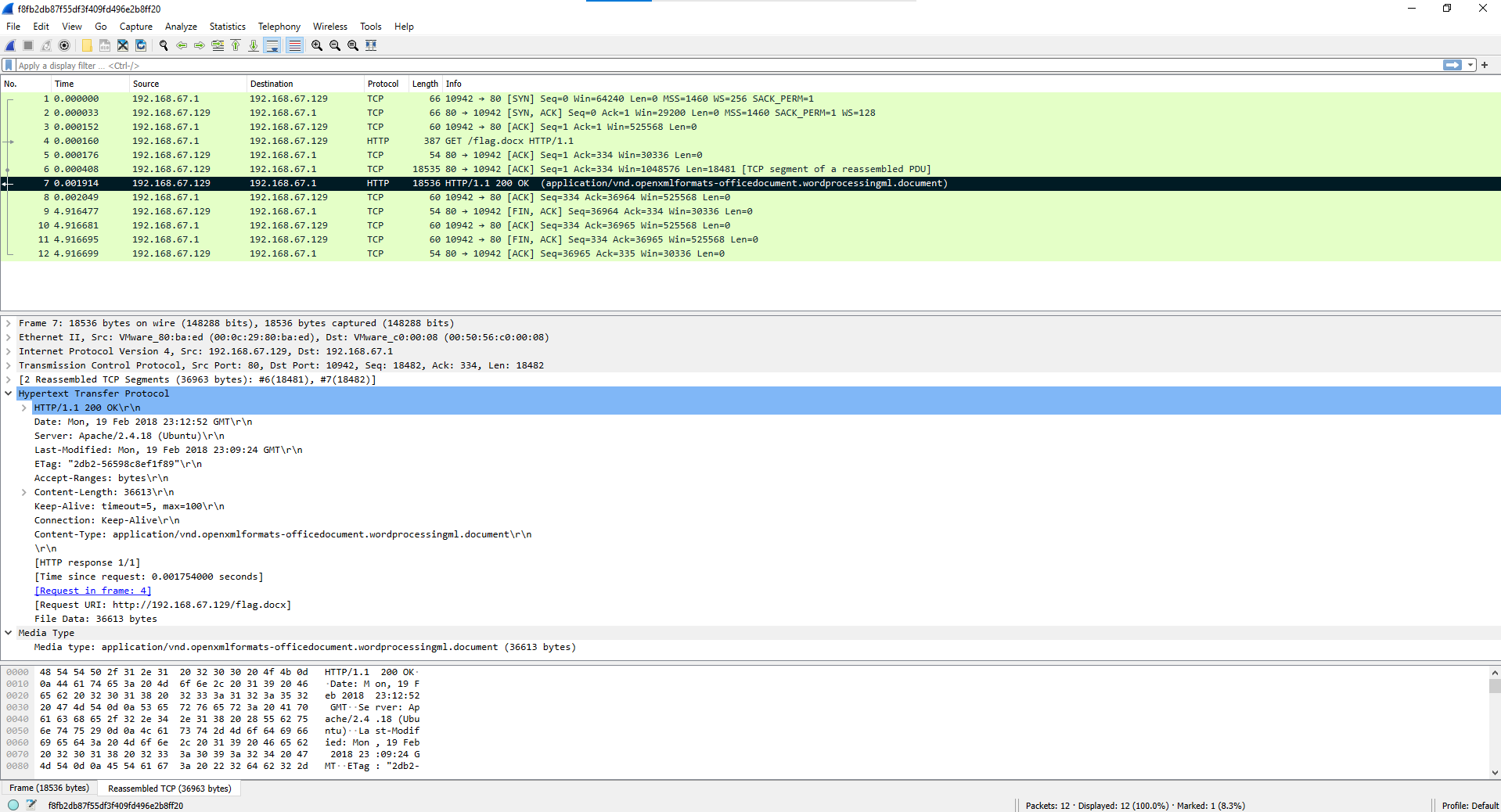
In order to view more details, I clicked on the HTTP response for that docx transfer. I found the “Media Type” entry payload in the display window of Wireshark and selected the “Show packet bytes” option from its corresponding options menu.
This dialog will allow us to load the unaltered data stream into a different program for further examination. In the “Show as” dropdown menu I select “Raw”. The display changes the packet view from ASCII to HEX data. However, if we use the “Save as” action, it will result in a binary file. We can save the file as “[file_name].docx”. Since DOCX files are really Zip archives of XML files, we can rename the file to use the .zip extension and explore the directories for the flag.
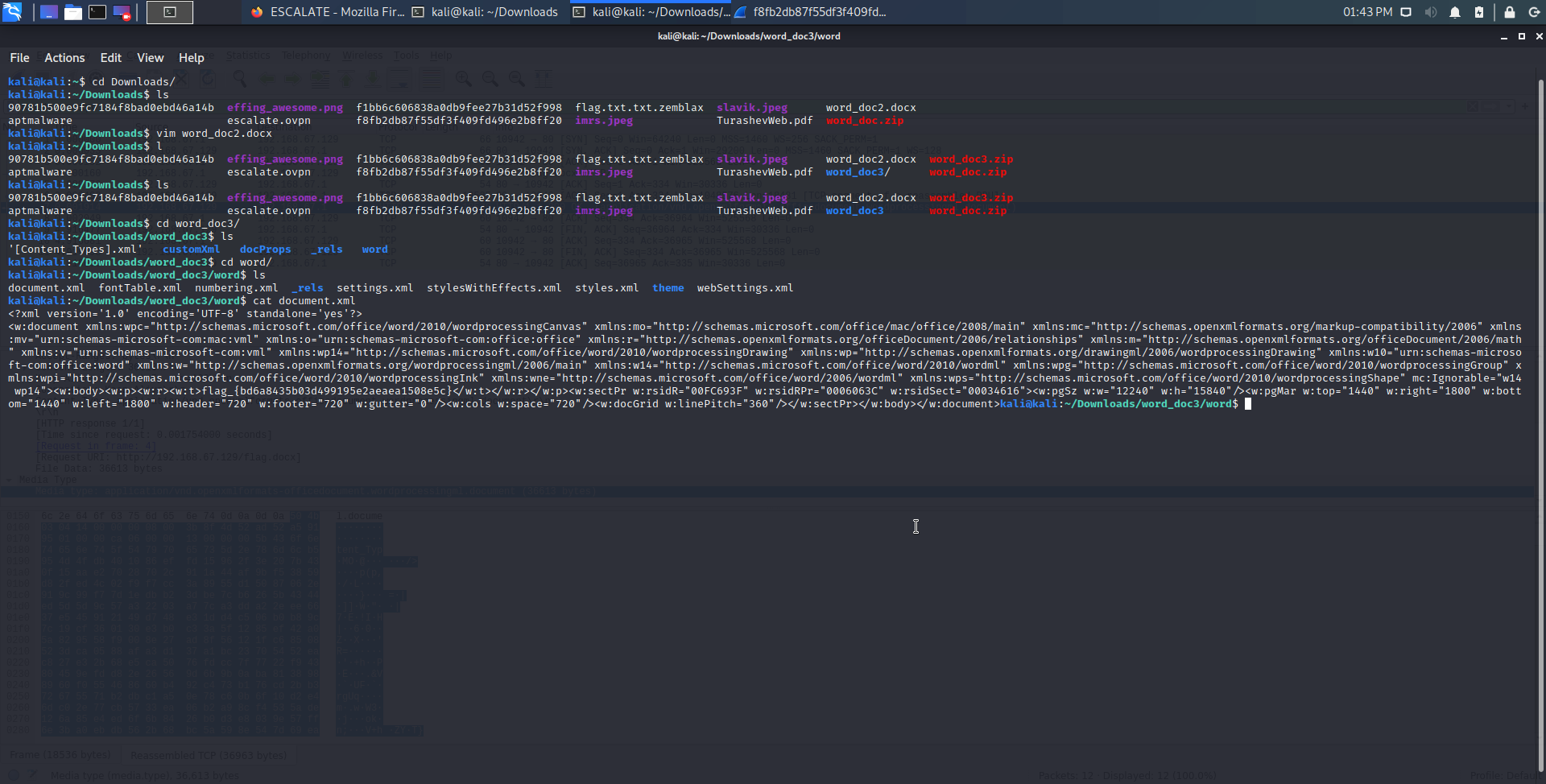
Unzip the file manually or via the terminal using the “unzip” Linux command. Several XML files are uncovered, showing a standard docx file structure. The flag was in the word/document.xml file.
flag_{bd6a8435b03d499195e2aeaea1508e5c}